CuMesh:
CuMesh Architecture comprises highly integrated information functions that enable it to operate as a cloud service or as an internet cell with IoT.
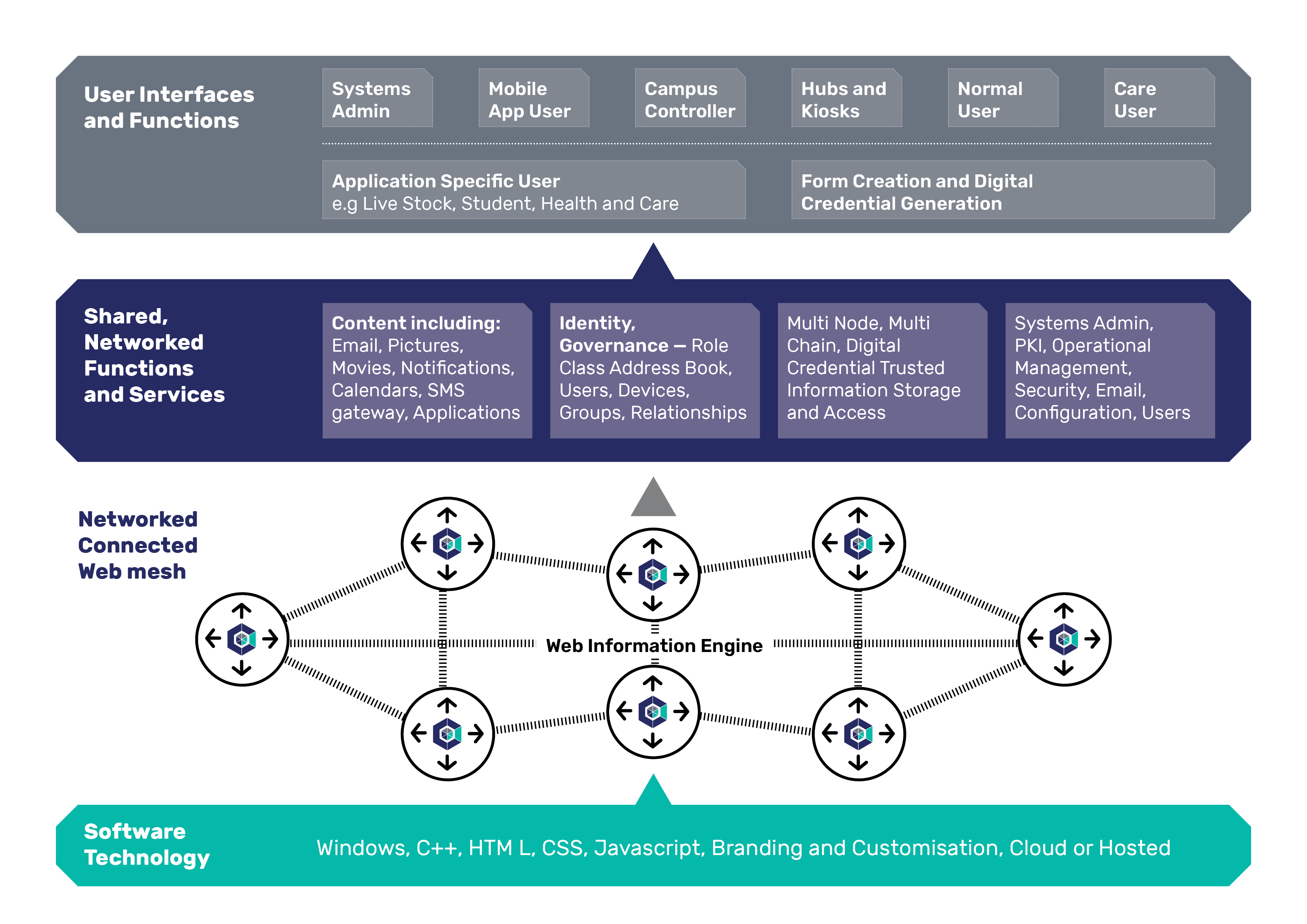
CuMesh Architecture - the Functional - Layered View
CuMesh contains many key and advanced functions including the ability to soft configure parameterised web forms and mobile applications and screen designs.
Functions include: identity, user management, content, email, SMS, digital asset multi chains, documents, images, videos, stream cameras, IoT devices, social groups, systems management
CuMesh design is native IoT - its elements, data sets, users, devices are web-URL addressable
The CuMesh Architecture can be represented from different perspectives.
The list below provides the key architectural perspectives.
- CuMesh Architecture - Information Sharing - Internodal View
- CuMesh Architecture - Web Forms Application Processing View
- CuMesh Architecture - Integrated Identity , PKI, Systems Management and Digital Asset Architecture View
- CuMesh Architecture - Zero Trust Architecture View
- CuMesh Architecture - BIM, ISO 19650, Victoria Digital Asset Strategy - Construction CDE View
- CuMesh Architecture - Live stock and Agri Tech Application including Digital Assets
- CuMesh Architecture - Aged Care, Accessibility and Social Inclusion **
** The CuMesh (Cuuble) Aged Care application applies WCAG 2.0 accessibility standards.
Accessibility functions for online platforms are mandated via regulations.
CuMesh design has embraced cyber security, trusted systems and digital asset engineering.
CuMesh is a networked web engine. It places the maximum cyber security protection to edge applications in line with the USDOD ZTA initiative.
Tightly integrated functions, development tool sets and work flows reduce the attack surfaces of a system significantly.
- 2FA logon security as a profile selected option
- Ability to operate off net – without the Internet
- Soft Configured, mesh wide role, title, class, genre identity relationship system **
- Digital asset cross node/chain transfer controls
- Dynamic session key creation (masquerade prevention)
- Supports the USDOD ZTA agenda
- Full range of diagnostics, logs, statistics and alarms
- HTTPS web protocols and WC3 CSP (Content Security Policies)
- Triple level PKI signing of digital assets (legally verified provenance)
- Inbuilt mesh, node systems management functions
- Integrated smart mesh PKI /X.509 Certificate Authority (CA) functions
- Intrusion detection and attack prevention
- Proprietary encryption on personal and inter-node data
- Scale achieved by meshed multi nodes, cloud operations
- Inbuilt content management, email and IoT functions
- User key and certificate statistics and management
- User level profiles and accessibility options
- Rapid end user mobile application development
- Web page designs can be restyled and branded
- Click through user experience and work flows
- Demonstrable and can be tested on a desk top PC
** Role based identity - essential for formalised Governance, Regulation and Digital Asset processes.
Begin the transformation journey..